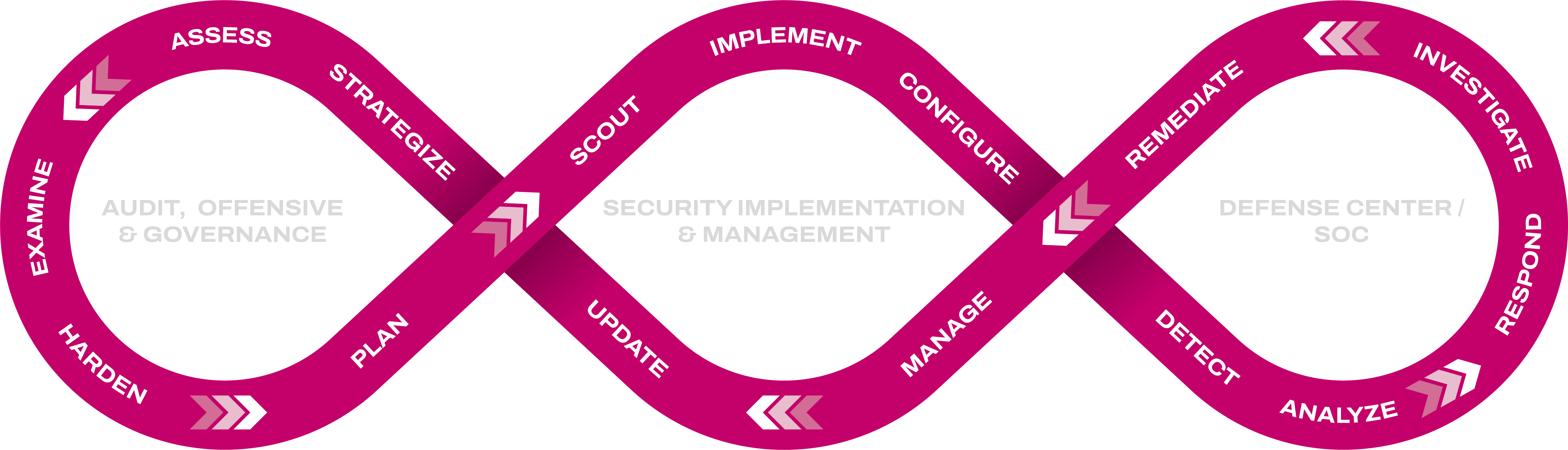
In an increasingly threatened industrial landscape, where critical infrastructure sectors are frequently targeted, our industrial security solutions address the unique challenges faced by organizations. From threat intelligence to proactive defense measures, we empower you to safeguard your critical assets and prevent costly breaches.
With our expertise and in-depth knowledge of OT/ICS environments, we help you navigate the complex and rapidly evolving industrial cybersecurity landscape effectively, ensuring the resilience and safety of your operations.
Solutions
OT case study
Check security solutions for
Do you want to learn more
or schedule a call for expert consultancy?
Fill out the form below.