
It is estimated that Google has stored more pages than any other search engine in the world. With more than billions of pages and a relatively low execution time, the popular Californian search engine manages to satisfy all searches, whether performed for curiosity or for less harmless purposes. It is so powerful that it can categorise over 15 million pages in less than a minute.
Moreover, it is assumed that 60+ thousand searches are conducted through Google’s search engine every second. This means over 1 trillion searches per year. These are astronomical numbers that Google manages to keep up with thanks to the enormous infrastructure it has set up.
Certainly, search engines have turned many people’s lives upside down; having so much information in the space of 1 minute is food for thought for anyone. But the most surprising thing, despite these numbers, is that we exploit only a very small part of the potential that this tool offers us.
Few people know that Google has a proprietary language to extract information beyond the normal keyword search. Even with little knowledge of Google keywords, you can find much more information than you ever imagined. Let’s look at some of them.
What are Google Dorks
Dorks are defined as search queries that, instead of simply containing a description of what we are looking for, are also composed of several keywords that allow us to refine the parameters of the search in order to obtain specific results.
Purposes for which they are used
As mentioned, dorks are mainly used to refine search results, in order to have a more specific list of links. For instance, let’s try searching for ‘pizza napoletana’. The simple word ‘pizza’, searched on Google, has more than 1,360,000,000 results, while combined with the word ‘napoletana’, the results drop dramatically (still more than 15 million). This is already an attempt to refine our search and narrow the search field.
Starting from the assumption that some sysadmins may not have applied certain rules, it is possible to search for certain confidential and/or reserved files, not intended for the general public on the Internet. Be careful, however: although some webmasters expose sensitive information on their own, this does not mean that it is legal to exploit it in order to gain an advantage (economic or not). Simple consultation is not a crime, but exploitation is and is prosecuted. It is quite easy to trace the surfing IP, even if a VPN service is used.
Many vulnerabilities are searched for by script kiddies precisely through Google. A careful query in fact searches for error messages, configuration files or anything else that could somehow expose software versions or confidential data to the outside world.
Some examples of dorks
| Dorks name | Description | Example |
| site:domain | results will be files and pages present in the domain “domain” | site:w3school.com |
| intitle:word | results will contain in the title the word after the dork “intitle” | intitle:hi |
| inurl:word | results will contain in the title the word after the dork “inurl” | inurl:gallery |
| intext:text | results will contain pages with the searched “text” | intext:“Index of” |
| ext:extention | results will contain files with the requested extension | ext:jpg |
| filetype:type | results will contain files with the extension specified by type | filetype:pdf |
| cache:url | redirects the user to the Google cache of the specified url | cache:cyberhood.eu |
| info:root_domain | the result will contain the root domain and all related information | info:amazon.com |
It should be mentioned that dorks can be concatenated to further refine our search, such as ext:ini intext:env.ini or ext:mdb inurl:*.mdb inurl:fpdb shop.mdb .
Google Dorks for SCADA
It must be said that there is no single Google dork that will reveal every SCADA interface that exists on the network, this is because it depends very much on the manufacturer and the products used. Each company creates its own embedded systems with proprietary features. They share common protocols and procedures, but in general they are unique objects.
Some of the main manufacturers are: Siemens, Schneider Electric, Rockwell Automation, GE. In addition to this, it must be considered that each of these companies makes several products belonging to the same family, so research requires that specific Google Dorks are developed for each of them. Below is a brief summary of some of the main brands and their queries.
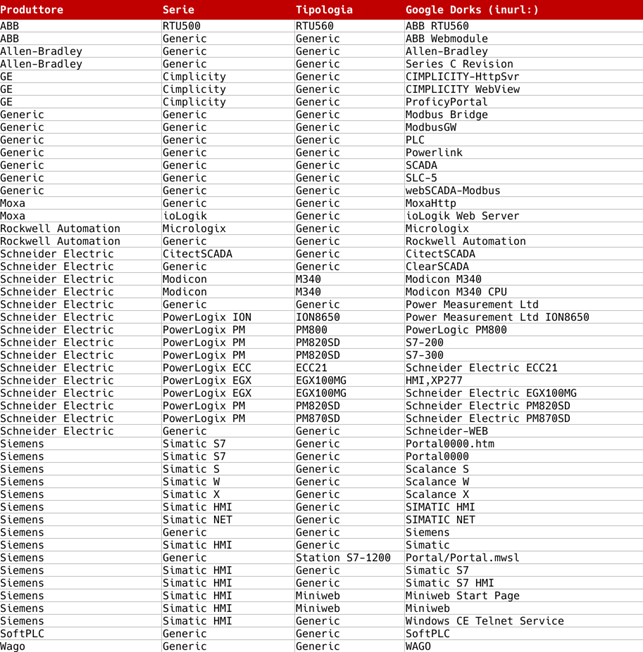
Using Google Dorks
Now let’s try some dorks to find specific SCADA systems, starting with one of the most widely used products in automation systems in Italy: Siemens’ S7 series PLC, which is the same family of controllers that were the target of the infamous Stuxnet attack against Iran’s Natanz nuclear power plant in 2010, probably the most sophisticated SCADA attack to date.
Our Google Dork looks like this: inurl:/Portal/Portal.mwsl
When we use it in a Google search, we get the results shown below.
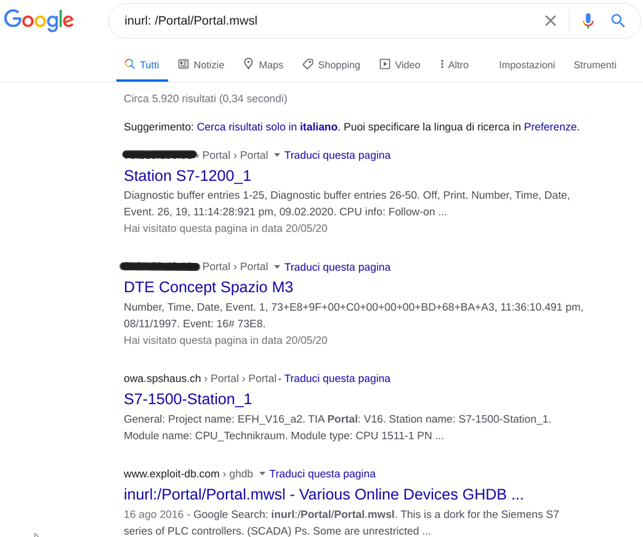
If we select the first item in the list (Siemens S7-1200_1) we access the following page:
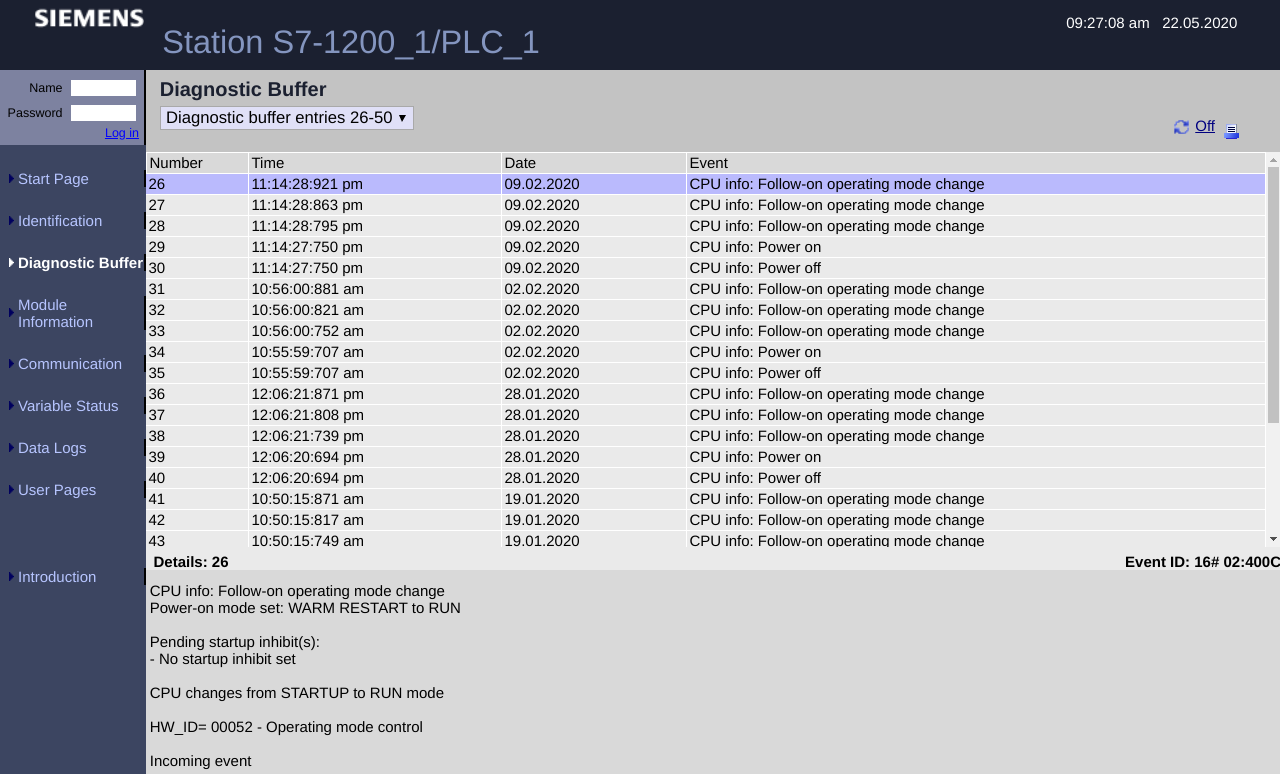
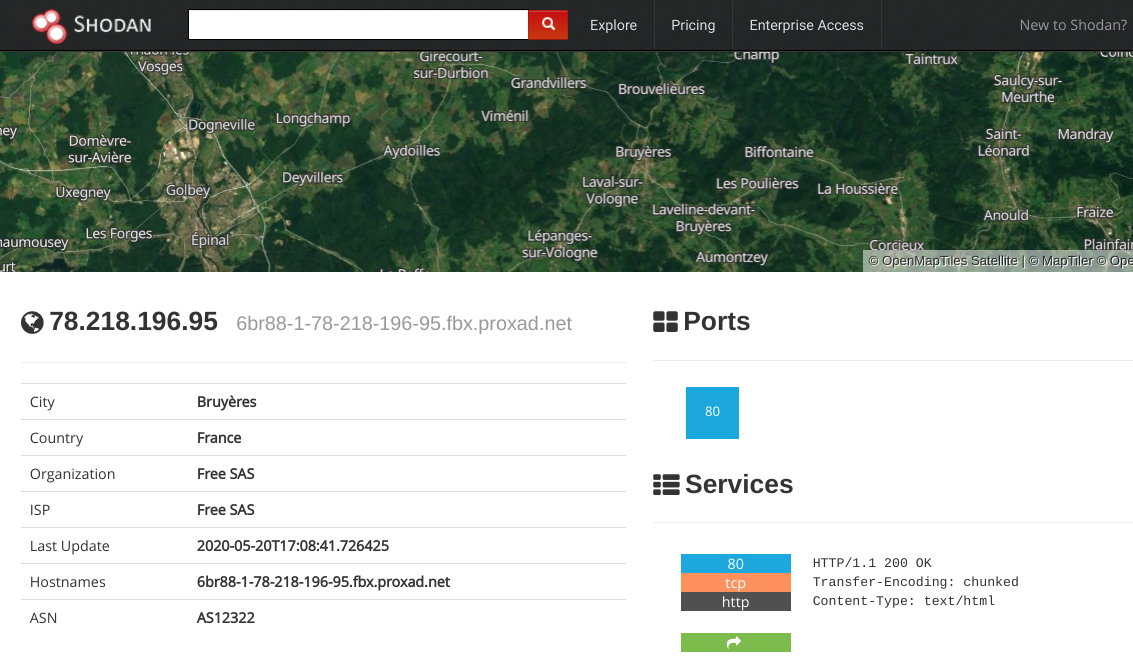
This seems to be the Siemens S7 PLC administration portal somewhere in the world. To continue our search, we enter the IP address Google gave us (XX.XXX.XXX.XX) into Shodan to see where it is located. It is in Bruyères, France.
When clicking on the “Identification” tab on the left, the PLC identifies itself as an S7-1200_1/PLC_1 station. It also gives us the serial number and firmware version (thus simplifying a possible attack).
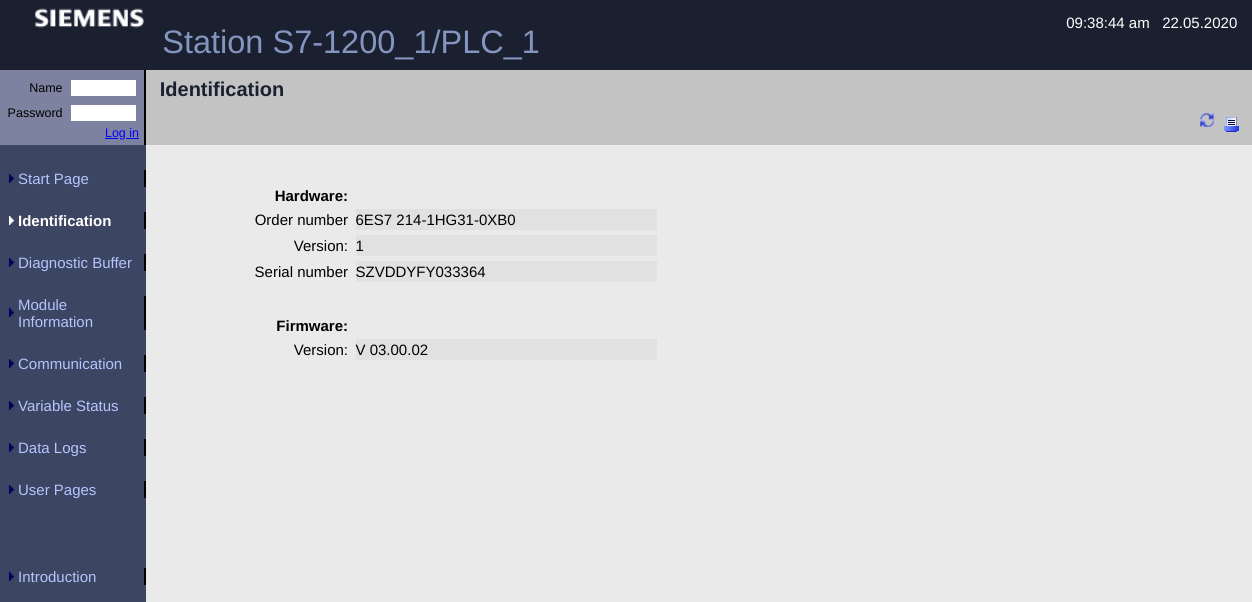
The same thing happens if we click on “Communication” from the menu on the left.
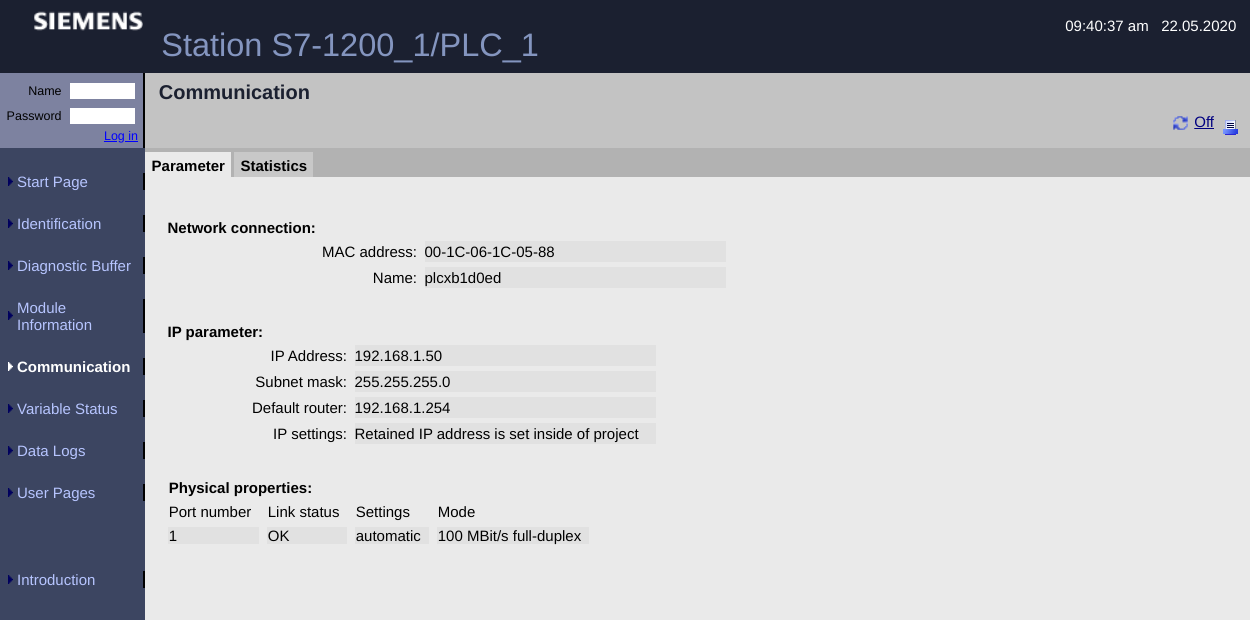
As we can see, the security of ICS systems is still at an early stage, relying mainly on security by obscurity. These simple Google Dorks too easily expose critical systems without the slightest security criterion. Even a hacker with basic skills can access control systems and create chaos.
So what to do to improve your ICS security?
In this context, we have two different types of measures that can be taken: some are more procedural – such as Security Assessment, specific OT/ICS & Awareness training, policies for Secure Access Management – while others are more technical, including Asset Inventory & Vulnerability Scanning, Network Segmentation & Monitoring, secure programming of PLCs, as well as patching, backups and recovery plans. Additionally, it is essential to stay up to date on the latest cybersecurity threats and best practices to ensure that ICS systems remain secure and resilient.
Important Note
The purpose of this article is educational and informative. Any unauthorised action against any control system on a public or private network is illegal. The information contained in this article is intended to make it clear how necessary it is to improve defence systems, and not to provide tools for attacking them. Breaking into a computer system is punishable under criminal law and can cause serious damage to property and persons, especially when it comes to ICS. All tests shown in the tutorials were carried out in isolated, secure, or manufacturer-authorised laboratories.









