THANK YOU!
You will receive via e-mail
the link to download the White Paper
Do you want to discover more about cyber security and HWG Sababa? Read our Blog! Below you can find the most popular articles.
HWG Sababa, a leading company in the cybersecurity sector, hosted forty MBA students from Hofstra University in New York at its Milan headquarters for a day of discussions on strategic…
The arrival of 5G technology marks a new era of connectivity, bringing with it promises of lightning-fast internet speeds, seamless communication and transformative advancements across various sectors. By 2025, 5G…
In today's digitally interconnected landscape, organizations heavily depend on networks of suppliers and partners to maintain operations and foster innovation. However, without adequate attention to cybersecurity resilience in the supply…
HWG Sababa, an internationally recognized cybersecurity provider , will be participating in the prestigious PLUS-Forum “Digital Uzbekistan” for the third consecutive time. The event is set to take place in…
In an era where digital manipulation is predominant, the rise of deepfake technology has created a new frontier of deception. Deepfakes blur the lines between reality and fiction with unprecedented…
Taking place from April 23 to 25 at the Dubai World Trade Centre, GISEC Global 2024 is a leading event in the cybersecurity realm of the MENA region. It brings…
In 2023, the healthcare industry was ranked as the fourth most impacted by successful and publicly disclosed cyber-attacks[1], falling behind Manufacturing, Professional/Scientific/Technical, and ICT industries. Accounting for 9% of the…
In today's digitally driven world, the demand for cybersecurity professionals is higher than ever, and this urgent need is underscored by projections indicating a potential shortfall of approximately 3.5 million…
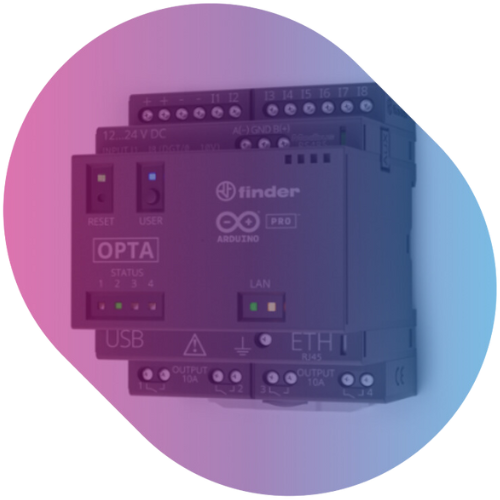
Arduino is a world leader in open-source hardware and software, with millions of developers worldwide. The Arduino ecosystem has been chosen for IoT, Industry 4.0, AI and ML projects on…
By 2030, it is estimated that there will be over 29 billion connected devices worldwide (source: Statista). Inevitably, these devices will need to be as secure as possible to avoid…